
The attack, named Pixnapping, works by reading what’s displayed on your screen—pixel by pixel—without needing any special permissions.
How the Attack Works
Pixnapping exploits weaknesses in how Android displays information on your screen. A research team from UC Berkeley, Carnegie Mellon, and other universities discovered that malicious apps can reconstruct sensitive data by measuring tiny timing differences in how pixels are rendered.
The attack happens in three steps. First, a malicious app triggers another app (like Google Authenticator) to display sensitive information. Second, it overlays semi-transparent windows and uses Android’s blur API to manipulate individual pixels. Third, it measures rendering times through a hardware weakness called GPU.zip to steal pixel values one at a time.
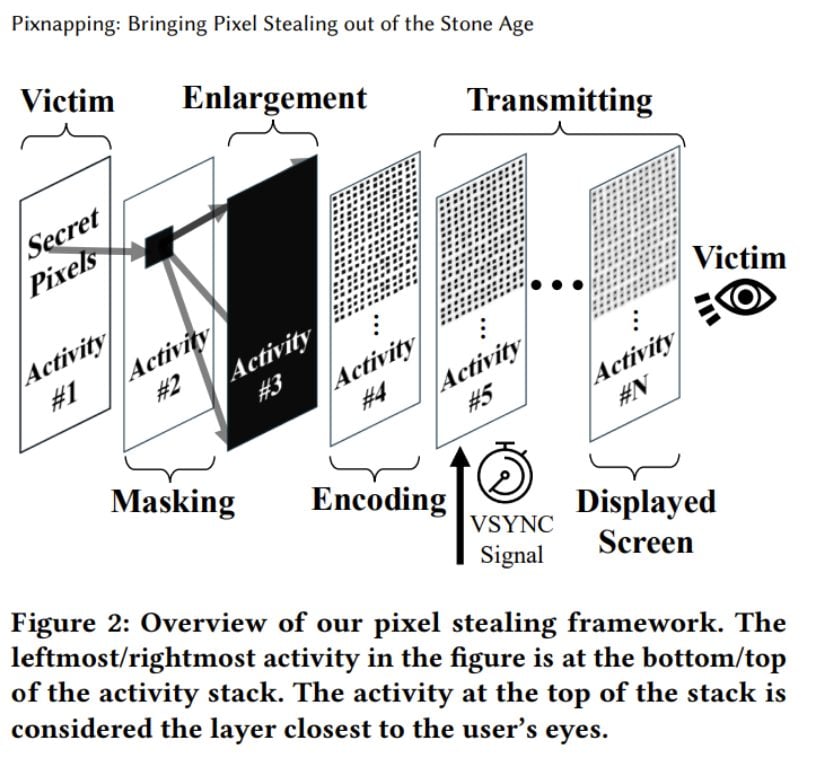
Source: pixnapping.com
Think of it like taking a screenshot, but instead of capturing the whole screen at once, the attacker reconstructs the image pixel by pixel by measuring how long each one takes to draw. The malicious app doesn’t need screen recording permissions or notification access—it simply exploits standard Android features that most apps can use.
Real-World Testing Results
Researchers tested Pixnapping on five devices: Google Pixel 6, 7, 8, and 9, plus Samsung Galaxy S25. All ran Android versions 13 through 16. The results were concerning for Pixel owners. On Pixel devices, the attack successfully recovered full six-digit 2FA codes in 73% of attempts on Pixel 6, 53% on Pixel 7 and 9, and 29% on Pixel 8. Recovery times ranged from 14 to 26 seconds—well within the 30-second window that most authentication codes remain valid.
Interestingly, the Samsung Galaxy S25 proved more resistant. Researchers were unable to recover codes within 30 seconds on this device due to noise in its graphics hardware. The team demonstrated successful data theft from popular apps including Google Authenticator, Signal, Venmo, Gmail, and Google Maps. Any information visible on screen becomes vulnerable, from private messages to location data.
Critical Threat to Crypto Wallets
For cryptocurrency holders, this vulnerability poses a major risk. Wallet seed phrases—the 12 or 24 words that grant complete access to your crypto—are especially vulnerable because users typically leave them displayed while writing them down for backup.
While stealing a full 12-word phrase takes longer than grabbing a 2FA code, the attack remains effective if the phrase stays visible. Once attackers have your seed phrase, they control your entire wallet. No additional passwords or security measures can stop them from draining your funds.
Hardware wallets remain the safest option because they never display seed phrases on internet-connected devices. The private keys stay isolated in the hardware device, signing transactions without exposing sensitive information to your phone or computer.
Current Patch Status
Google learned about Pixnapping in February 2025 and assigned it CVE-2025-48561, rating it high severity. The company released a partial fix in September 2025 by limiting how many times apps can use blur effects—a key component of the attack.
However, researchers found a workaround that bypasses Google’s first patch. Google confirmed it will release another update in the December 2025 security bulletin to address remaining vulnerabilities.
The good news: Google reports no evidence of real-world attacks using Pixnapping. Their Play Store security systems haven’t detected any malicious apps exploiting this vulnerability. But the attack remains possible on unpatched devices.
Samsung devices also received the September patch. Researchers notified Samsung that Google’s initial patch was insufficient to protect Samsung devices from the original attack. Both companies continue coordinating on additional protections.
Protecting Your Assets
No special mitigation exists yet for individual apps to defend against Pixnapping. The fixes must come from Google and Samsung at the system level. Meanwhile, several steps can reduce your risk:
Install security updates immediately when they arrive. The December patch should significantly improve protection for compatible devices.
Download apps only from Google Play Store, avoiding unknown APK files from websites or third parties. Review what permissions your apps request—though Pixnapping doesn’t need special permissions, limiting app access still improves overall security.
Never display crypto wallet seed phrases on any internet-connected device if possible. Write them down on paper immediately rather than leaving them on screen. Better yet, use a hardware wallet for storing significant cryptocurrency holdings.
Consider the broader security landscape. This year has seen major crypto theft, with billions lost to various attacks. Mobile security represents just one vulnerability among many.
The Bigger Picture
Pixnapping reveals fundamental weaknesses in how Android handles window layering and graphics rendering. The attack exploits data compression in Mali GPUs used by Pixel phones—compression creates timing variations that leak information about pixel values.
Other Android phone manufacturers likely face similar risks since the necessary mechanisms exist across the Android ecosystem. The research team hasn’t tested all brands yet, but the core APIs enabling the attack are standard Android features.
The underlying GPU.zip hardware vulnerability remains unpatched. No GPU manufacturers have committed to fixing the compression timing leak that makes Pixnapping possible.
Researchers will release their proof-of-concept code on GitHub once patches are widely available.
Bottom Line
Pixnapping demonstrates that even apps without suspicious permissions can pose serious threats. For crypto users, the message is clear: keep seed phrases off your phone. Use hardware wallets for serious holdings. Install updates promptly. And remember that convenience often conflicts with security—protecting your crypto requires taking extra steps that might feel inconvenient but could save you from total loss.

























 24h Most Popular
24h Most Popular







 Utilities
Utilities